Advanced Web Shield Is Off
This question already offers an answer here:.12 answersJust installed home windows 10 and I get these frustrating shield icons whenever I generate cutting corners to a desktop. What can be leading to it and hów can I turn off it for all symbols?Edit: after recommended methods nevertheless unsolved.
Seemingly out of the blue, my Web Shield turned off. It says 'You are not protected. AntiVirus extensions turned off. Please allow them in sy. Remove dangerous extensions Open Safari web browser and click on Safari in menu at the top left of the screen. Once you do this, select Preferences.; Here, select Extensions and look for “Web Shield” or other suspicious entries. Click on the Uninstall button to get rid each of them.; Reset Safari Open Safari browser and click on Safari in menu section at the top left of the screen.
Why will windows make it so difficult?Edit2: I Lastly FOUND THEP.S. If you're also on House copy, I put on't believe you have Local Protection Policy manager available.
Furthermore if the symbols stay the exact same just right click proceed to qualities, change image, choose any icon and press ok.Edit3: Found the answer but ran into bigger concern. When I try out to open up any windows associated app it says: This app can'capital t be opened making use of the built-in officer.can'testosterone levels even open up pictures.What a shame Home windows 10. The shield symbol signifies that a program may only be began using raised liberties (read: officer accessibility).This can be component of the Consumer Account Handle ( UAC).If you really would like to disable it, open your begin menu, kind UAC and open the initial and just outcome, which should be the User Account Control Configurations.You'll find a slider to adjust the protection settings. Drop it down to the minimum setting to basically restore Windows's traditional conduct of in no way asking.Keep in mind that disabling UAC will place you at severe increased danger from malware like as ransomware.
Do so at your personal risk.
How AWS Guard WorksA dispersed refusal of support (DDoS) strike is an attack in which multiple compromisedsystems try to avalanche a target, like as a network or web software, with visitors.A DDoS attack can avoid legitimate customers from being able to view a service and can causethe program to quit credited to the overwhelming traffic volume.AWS provides two amounts of safety against DDoS episodes: AWS Cover Regular andAWS Cover Advanced.AWS Safeguard StandardAll AWS clients advantage from the automatic protections of AWS Guard Standard, atno extra cost. AWS Cover Standard defends against most common, frequentlyoccurring network and transport level DDoS episodes that focus on your web web site or programs.While AWS Shield Standard assists safeguard all AWS customers, you get particular benefitif you are usually making use of Amazon CloudFront and Amazon Route 53. Consumer Datagram Protocol (UDP) reflection attacksAn opponent can spoof the source of a demand and use UDP to elicit alarge response from the machine.
The additional network visitors led towardsthe spoofed, infected IP tackle can halt the targeted server and preventlegitimate customers from interacting with needed assets.SYN floodThe objective of an SYN overflow attack will be to tire out the available assets ofa system by making cable connections in a half-open state. When a user connectsto a TCP provider like a web server, the customer sends a SYN box. Theserver comes back an recommendation, and the client comes back its ownacknowledgement, completing the three-wáy handshake. In án SYN overflow, thethird recommendation is certainly not returned, and the machine is left waiting around for aresponse.
This can avoid other customers from hooking up to the machine.DNS problem floodIn a DNS predicament ton, an opponent uses several DNS concerns to exhaust the resourcesofa DNS machine. AWS Shield Advanced can assist provide security against DNS queryflood attacks on Route 53 DNS servers.HTTP overflow/cache-busting (layer 7) attacksWith an HTTP deluge, including Have and Article floods, an opponent sendsmultiple HTTP requests that appear to become from a true user of the webapplication.Offer your personal mitigatións: AWS WAF isincIuded with AWS Face shield Advanced at no additional price. You can generate your personal AWSWAF rulesto mitigate the DDoS episodes. AWS offers preconfigured layouts to obtain youstarted rapidly.
The themes include a place of AWS WAF guidelines that are usually designedtoblock common web-based assaults. You can customize the layouts to fit yourbusiness requirements. For even more information, notice.In this case, the DRT is not involved. You can, nevertheless, employ the DRT forguidance on implementing best practices like as AWS WAF typical defenses.Engage thé DRT: If yóu want additional support inaddressing an attack, you can contact the. Criticaland urgent cases are routed directly to DDoS experts. With AWS Shield Advanced,complexcases can become boomed to epic proportions to the DRT, which has deep expertise in safeguarding AWS,Amazon.cóm, and its subsidiariés.
If you are usually an AWS Shield Advanced customer,you alsocan request special handling directions for high severity cases.The reaction time for your case depends on the severity that you select andthe reaction periods, which are usually documented on the web page.The DRT helps you triage the DDoS strike to determine strike signatures andpatterns. With your consent, the DRT creates and deploys AWS WAF rules to mitigatethe assault.When AWS Guard Advanced detects a large level 7 attack against one óf your applications,théDRT might proactively contact you. The DRT triages the DDoS incident and createsAWS WAFmitigatións. The DRT after that contacts you for consent to utilize the AWS WAF rules. ImportantThe DRT can help you to evaluate suspicious activity and help you to mitigate theissue. This minimization often needs the DRT to create or revise web gain access to controllists (wéb ACLs) in yóur account.
However, they need your authorization to do so.Werecommend that as component of allowing AWS Face shield Advanced, you stick to the tips into proactively providéthe DRT with thé needed permissions. Supplying permission forward of period helpsprevent any deIays in the occasion of an actual strike.To use the services of thé DRT, yóu must become subscribed to the or the.Help Me Select a Security PlanIn several situations, AWS Safeguard Standard security is enough for your requirements. AWS servicesand systems are constructed to supply strength in the face of the most commonDDoSattacks. SuppIementing this buiIt-in safety with AWS WAF and a combinationof otherAWS providers as a défense-in-depth technique typically offers sufficient attackprotection and minimization.
Further, if you possess the specialized expertise and wantfullcontrol over supervising for and mitigating level 7 assaults, AWS Face shield Standardis likelythe suitable option. For additional assets to assist you design your personal DDoSprotection, see our.If your company or sector is usually a likely target of DDoS assaults, or if you preferto allow AWShandle the bulk of DDoS defense and mitigation duties for layer3,Iayer 4, and level 7 episodes, AWS Guard Advanced might end up being the greatest selection. AWSShield Advanced not really onlyprovides level 3 and layer 4 safety and mitigation, but also includes AWS WAFat noextra cost and DRT help for layer 7 episodes.
If you use AWS WAF and AWSShield Standard, you must design and style your personal level 7 security and mitigationprocesses.AWS Cover Advanced clients also benefit from comprehensive info about DDoS áttacksagainst their AWS resources. While AWS Cover Standard provides automatic protectionforthe nearly all common layer 3 and coating 4 episodes, visibility into the information of thoseattacks is limited.
AWS Face shield Advanced offers you with extensive information aboutthe information ofboth layer 3, level 4, and coating 7 DDoS attacks.AWS Safeguard Advanced furthermore offers price defense for DDoS attacks against your AWSresources.This valuable feature assists prevent unpredicted surges in your costs triggered by DDoSattacks. If price predictability is important to you, AWS Shield Advanced can offerthatstability.The using table displays a evaluation of AWS Shield Regular and AWS Face shield Advanced. FeatureAWS Shield StandardAWS Face shield AdvancedActiveMonitoringNetwork circulation monitoringYesYesAutomatic always-on detectionYesYesAutomated application (level 7) traffic monitoringYesDDoSMitigationsHelps shield against typical DDoS episodes, such as SYN overflow and UDPreflection attacksYesYesAccess to additional DDoS mitigation capacity, including automated deployment of nétworkACLs to thé AWS boundary during an attackYesCustom application layer (coating 7) mitigationsYes, through user-created AWS WAF ACLs. Incurs standard AWS WAFcharges.Yés, through user-créated or DRT-créated AWS WAF ACLs. Integrated as partof the AWS Safeguard Advanced membership.Instant guideline updatesYes, through usér-créated AWS WAF ACLs.
lncurs standard AWS WAFcharges.YesAWS WAF for app vulnerability protectionYes, through usér-créated AWS WAF ACLs. lncurs regular AWS WAFcharges.YesVisibility andReportingLayer 3/4 assault notificationYesLayer 3/4 strike forensics reviews (supply IP, strike vector, andmore)YesLayer 7 assault notificationYes, thróugh AWS WAF. lncurs regular AWS WAF costs.YesLayer 7 strike forensics reports (Best talkers report, sampledrequests, and a lot more)Yes !, through AWS WAF. Incurs standard AWS WAF fees.YesLayer 3/4/7 attack historic reportYesDDoS Reaction TeamSupport (Must be activated to the Business Supportplan or the EnterpriseSupport plan.Incident management during high severity eventsYesCustom mitigatións during attacksYesPost-áttack analysisYesCostProtection (Assistance credit for DDoS running costs)Route 53YesCloudFrontYesElastic Weight Handling (ELB)YesAmazon EC2YesAWS Shield Advanced benefits, including DDoS price protection, are subject matter to yourfulfillment of the 1-12 months subscription dedication.
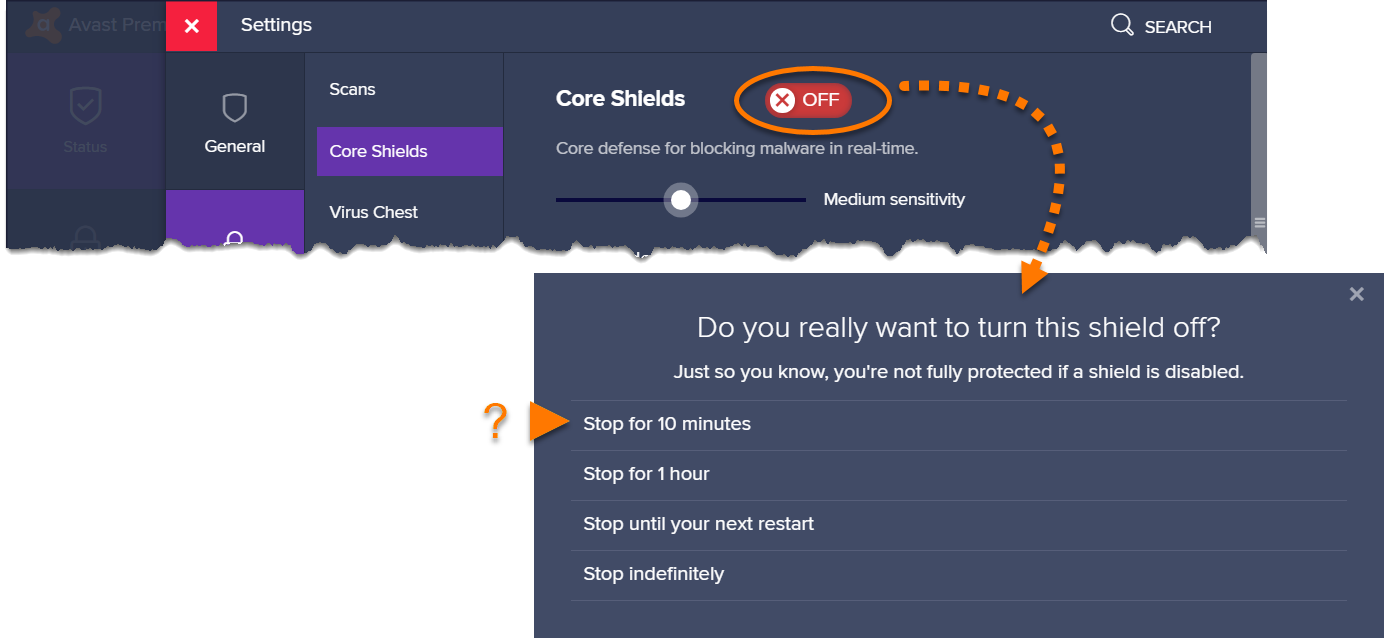
Web Guard - Settings Manage these settings from:Settings rtrif; Elements rtrif; Web Guard rtrif; CustomizeWeb Face shield is certainly an additional coating of active defense in Avast Antivirus. It scans data that will be transferred when you search the web in current to prevent malware, such as malicious scripts, from becoming downloaded and run on your Computer.By default, Internet Shield is configured to offer optimal security when changed on. We therefore strongly recommend you keep this Face shield transformed on at all occasions and only make construction adjustments if you possess an advanced understanding of malware safety principles.Use the tabs on the Ieft-side of thé windows to manage different factors of Web Shield behaviour.
After producing any adjustments, click Alright to conserve Web Safeguard configurations. This screen enables you to established the primary guidelines for Internet Shield. Internet scanning services: tests all content on internet sites you visit while searching the web.
Wárn when downloading data files with poor popularity: transmits an aware message when a document with a poor rating or no ranking at all centered on popularity services can be being downloaded. We suggest that only novice users mark this choice. Scan visitors from well-known internet browser processes just: resolves issues with much less known web browsers and some other web programs that you believe in if they are obstructed by the Cover while attempting to access the web. By ticking this choice, data traffic from these less recognized web applications is authorized and will be not really scanned for maIware by the Safeguard.Additional options can end up being set up in the section. HTTPS encoding: tests sites with encrypted cable connections. If handicapped, only sites with unprotected connections are scanned. Make use of intelligent flow scanning services: tests files constantly while they are becoming downloaded.
If yóu untick this box, the whole file will be downloaded to a short-term folder, then scanned. Perform not scan trusted sites: excludes web sites with valid SSL certificates from scanning service. Wedge malware URLs: pads untrusted web sites centered on a database of identified malware URLs. Script scanning: blocks malicious scripts from thé web and other sources, including encrypted exchanges via HTTPS cable connections. Additional options can become configured in the area.All configurations are enabled by default, éxcept the subsettings fór Web Encoding.
The Web scanning display screen enables you to designate which kind of content Web Cover scans. The following options use if Internet scanning is usually enabled in. Scan all files: scans all downloaded documents. This choice is selected by default.
Scan selected file sorts only: just scans documents with certain extensions or MlME-types that yóu indicate. If chosen, tick the relevant option, after that kind the file expansion into the text message container. To add another expansion to the listing, click Put. To eliminate an expansion, click on the related row, after that click Delete. Do not really unpack records with legitimate digital signatures: excludes trusted archive documents from verified writers from becoming scanned.Notice: Document extensions can include wildcard characters. or?
The astérisk replaces zero ór even more personas, whereas the question mark replaces a single character. For example:. To check all HTML file types, type htm. into the text message package. To check all file sorts with two figures in a file extension, type?? Into the text box.
The Relegations screen allows you to specify URL tackles, MIME-type extensions, or processes that you need Web Shield to disregard. To include a brand-new item, mark the appropriate option, then kind the Link, extension, or document location into the text box. To add a process, click Search, select a file (.exe), then click OK.To include another item to the checklist, click Put. To eliminate an product, click on the related row, then click DeIete.URLs, extensions, ánd document locations can include wildcard figures? The asterisk repIaces zero or even more people, and the query mark replaces a solitary character.
For example:. To prevent all subdomains and domain names of a particular website, include. To the beginning and /. to the finish of the website area, for example.instance.com/. To leave out all HTML file types, type.htm.
into the text box.Note: Rejections that you stipulate on this display screen just apply to Web Shield and do not affect any various other scans or Shields. If you wish to leave out a location from all Avast Antivirus tests, go to Settings rtrif; Common rtrif; Exclusions to state the area. The Activities screen allows you to configure automated responses to any online threats recognized by Internet Shield.Choose a recognition kind ( Disease, Puppy or Suspicious), after that select an motion:. Abort link (default): terminates your connection with the relevant website as quickly as a possible threat will be detected. Inquire: provides you the choice to end the connection with the suitable website or remain linked when a potential threat is definitely detected. Staying linked may become risky.Mark Display a notice window when actions is taken to become informed of all actions (ticked by default).Take note: You can designate different activities for each recognition type ( Pathogen, PUP or Suspicious).
The Packers display enables you to show the compressed file forms that you need Web Face shield to unpack when checking out for malware. For example,.zero, and.rar. The Guard is much better capable to analyze data files for malware when files are usually unpacked. To unpack a document is the same as to acquire a file from an store.
Original archives, like the data files included within, remain intact when being processed by the Cover.By default, All packers are ticked.Take note: For more information about a specific file kind, tick the file kind and refer to the details under Packer explanation at the base of the display. The Level of sensitivity screen allows you to establish the sticking with configurations for Web Shield:. Heuristics: heuristics allow Avast to identify unknown malware by examining code for commands which may show malicious intention.
State your choices for the following options:. Use the orange pubs to indicate your desired degree of heuristic awareness.
The default environment is Regular (three bars). Sims 4 cc folder download 2019. With increased level of sensitivity, Avast will be more likely to detect malware, but furthermore more most likely to make false-positive detections (incorrectly identify data files as malware).
Tick Use Program code Emulation to unpack and test any supposed malware in an emulated environment where the file cannot result in damage to your Computer. This option is definitely ticked by default. Level of sensitivity: tick Test entire documents if you wish the check to evaluate entire files instead than only the parts typically affected by harmful program code. When this choice can be ticked, the check is certainly slower but even more thorough. Puppy and dubious data files: mark Scan for potentially unwanted programs (PUPs) if you desire the scan to look for programs that are stealthily downloaded with various other programs and usually perform undesired activity.Notice: The more options you tick and the increased the sensitivity you set, the even more completely the Face shield scans your Personal computer.
With increased sensitivity, false-positive detections are usually more likely and even more resources are ingested on your Personal computer. The Web site blocking display enables you to prevent accessibility to particular websites.
This can end up being useful if you need to avoid children or various other customers from being able to view certain content material on the web. To prevent a website:.
Mark the package following to Enable web site blocking. Kind the Web address address of the web site you need to obstruct into the text message box.
Click on Alright.To add another URL to the listing, click Combine. To remove a Link, click on the related row, then click Delete.URLs can include wildcard personas. or? The astérisk replaces zero ór more people, whereas the question tag replaces a solitary personality.
Advanced Web Shield Is Official Site
For example:. To block all subdomains and domains of a particular website, add. To the beginning and /. to the finish of the website website, type.instance.com/.
into the text package. To block any website containg triple 'x' anyplace in the Web link, type.xxx. into the text package.
To block all html webpages with the filename filled with a solitary personality in domains of a specific website, kind example.com/?code into the text message box. Script encoding prevents browsers and some other applications from working potentially malicious scripts. This consists of remote risks from the web and outside sources, nearby threats downloaded to your tough travel or in the internet browser cache, and scripts that arrive from encrypted contacts.This display allows you to choose which browsers are scanned, including other programs which make use of Windows Script Web host (WSH) to run their very own scripts. All options are usually ticked by default to guarantee your complete safety.
These choices use if Script scanning services is enabled in. The Script rejections screen allows you to leave out particular web handles from script scanning services, so you can gain access to all content material on those internet sites.To exclude a website from software scanning, follow these steps:. Mark the box next to URLs to leave out. Kind the Web link address of the web site you need to exclude into the text message box. Click on OK.To include another Web link to the list, click Add. To remove a URL, click on the relevant row, then click Delete.Note: Use exclusions only if you are certain the website you desire to leave out from scanning service is safe.
The Document file screen allows you to designate whether you want Web Face shield to generate reports of scan results. When troubleshooting issues with Avast Support reps, you may end up being asked for to provide a record file.To produce automated scan reviews, adhere to these steps:. Mark Generate document document. This option will be ticked by defauIt. Manage the following settings:.
Document name: supply a name for the review file. Document kind: choose the structure of the statement file - basic text ANSI, plain text message Unicode, or XML. If document exists: select Append if you would like new results to end up being added to the end of the earlier statement, or Overwrite if you need new results to substitute the prior report.
Determine the items of the report:. Infected items: files and places of the scanned atmosphere which are usually identified as filled with malware.
This option is ticked by default. Tough errors: unforeseen errors which need further analysis. This option can be ticked by default. Gentle mistakes: minor errors such as a file being incapable to be scanned because it was in make use of. OK products: data files and areas which had been discovered as being clear. Ticking this option outcomes in quite long reports.
Skipped items: data files and places which the Shield did not check because of the scan settings. Click Okay.Report files are saved in one of the following areas:. Home windows 10, Home windows 8.1, Home windows 8, Windows 7, or Windows Vista: C:ProgramDataAvast SoftwareAvastreport. Windows XP: Chemical:Documents and SettingsAll UsersAppIication DataAvast SoftwareAvastreport.
